Microsoft Sentinel provides insightful analytics and intelligence on security threats to businesses of all sizes. Microsoft Sentinel is an all-in-one tool for monitoring attacks, gaining insight into those attacks, actively seeking new threats, and responding to those new threats as they are discovered.
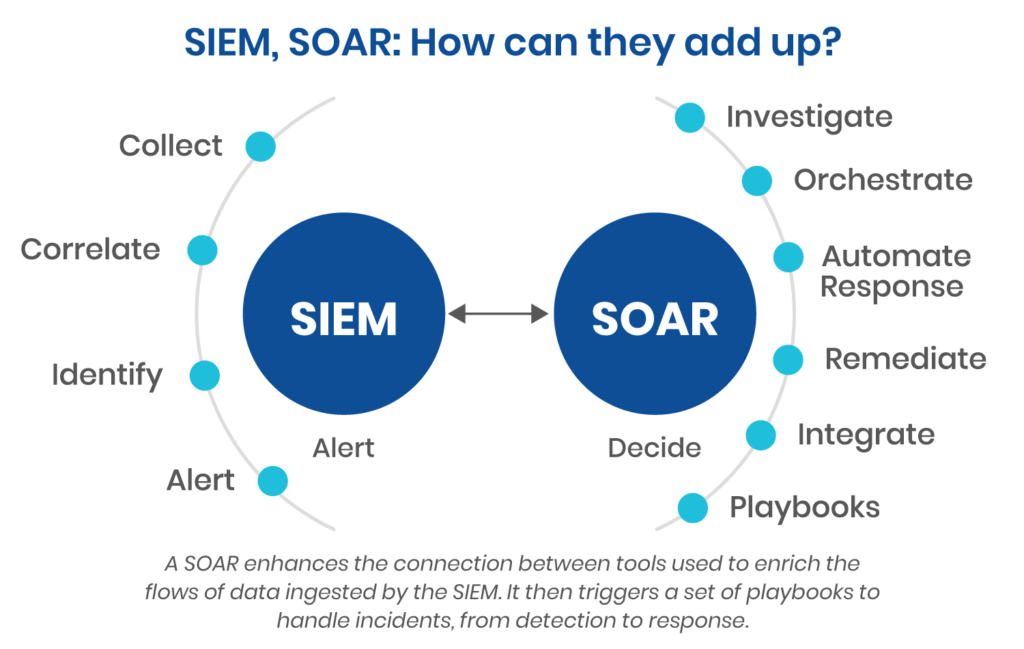
Security information and event management (SIEM) and Security orchestration, automation, and response (SOAR)
Azure Monitor’s tamper-proofing and immutability features have been incorporated into Microsoft Sentinel.
A security information and event management system (SIEM) is a tool for gathering, analyzing, and acting on information related to computer system security within an organization. These systems may consist of either hardware appliances or software applications.
SIEM : Log management, Alerting, Visualization, Incident management, Querying data
What is Microsoft Sentinel?
Microsoft Sentinel helps you enable end-to-end security operations including collection, detection, investigation, and response:
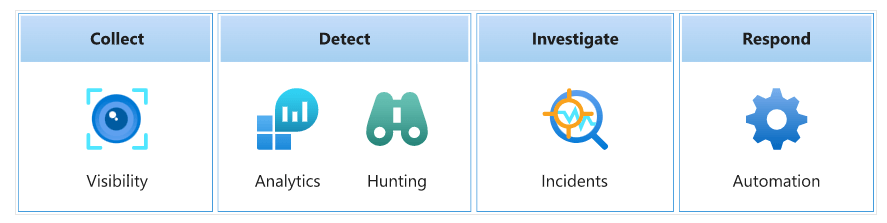
- Collect ( Visibility – Workbooks ): Data from all users, devices, apps, and infrastructure on-premises and across clouds must be collected. data connectors: common event format, Syslog, or REST-API.
- Detect ( Analytics (ML) and Hunting (Jupyter Notebooks) ): Microsoft’s analytics and threat intelligence can find undetected threats and minimize false positives.
- Investigate( Incidents (Mapping) ): Draw on Microsoft’s extensive history in cyber security to conduct AI-powered threat investigations and a broad-scale hunt for suspicious behaviors.
- Respond( Automation – Playbooks ): Quickly address issues using in-built orchestration and routine task automation.
Microsoft Sentinel uses Log Analytics and Logic Apps natively. AI enhances Microsoft Sentinel’s detection and investigation, data is stored by using Log Analytics.
Log Analytics is used to store your data, which is collected by Microsoft Sentinel. Using Log Analytics affords you the opportunity to query your data using the Kusto Query Language (KQL), which is one of the many advantages of this tool. KQL is a powerful query language that provides you with the capability to dig into our data and derive insights from it.
Workbooks – visualization (Collect)
Once you have signed up for Microsoft Sentinel, you can use the Azure Monitor workbooks integration to keep an eye on your data. Integrate playbooks with Azure Logic Apps to automate your responses to threats.
Microsoft Sentinel’s workbooks provide a visual representation of your data. Dashboards are what workbooks remind you of. An individual KQL query is used to construct each section of the dashboard. You can use one of the workbooks that came with Microsoft Sentinel, change an existing one, or start from scratch.
Microsoft Sentinel data can be seen in workbooks without coding. You can’t integrate workbooks with external data.
Analytics alerts – Machine Learning Models (Detect)
You have data visualization and logs. Now it would be great to have proactive analytics across your data to alert you when something suspicious happens. Analytics alerts can be enabled in your Sentinel workspace. Some alerts can be edited. Microsoft machine-learning models power other alerts. You can also make scheduled alerts from scratch.
Threat hunting – Notebooks / Jupyter Notebook (Detect)
There are predefined hunting queries available for use by SOC analysts that need to track down potentially malicious activities. Moreover, analysts have the option of writing their own queries. Azure Notebooks is another platform that Sentinel supports. For more experienced data explorers who want to utilize a programming language’s full capabilities, it includes example notebooks.
Notebooks have become the standard method for collaborating on data science and machine learning projects and for sharing and documenting results amongst team members.
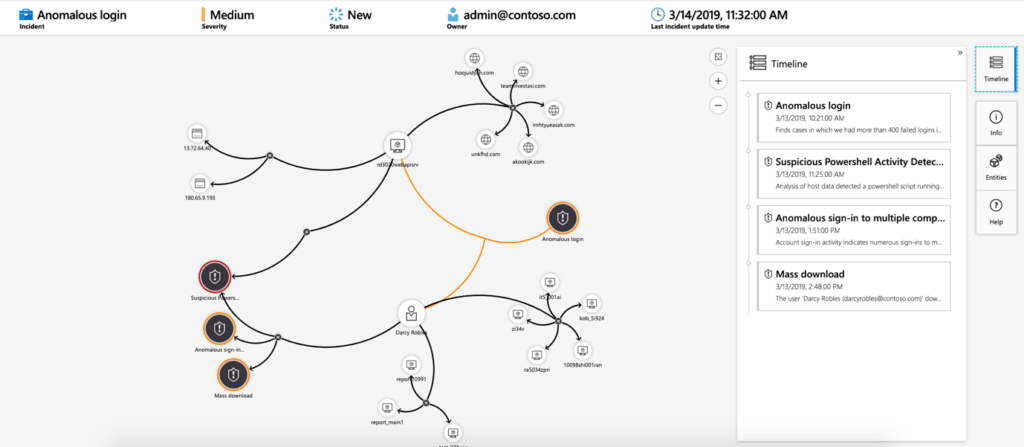
Incidents and investigations – Mapping (Investigate)
You have data visualizations and logs. It would be nice to have proactive analytics throughout your data to alert you when something suspicious happens. Analytics notifications can be enabled in your Sentinel workspace.
Activating an alert creates an incident. Change status or assign incidents to investigators in Microsoft Sentinel. Visually investigate incidents in Microsoft Sentinel by mapping entities across log data over a timeline.
Automation Playbooks (Respond)
Playbooks: A playbook is a collection of remediation actions that Microsoft Sentinel can perform as a routine.
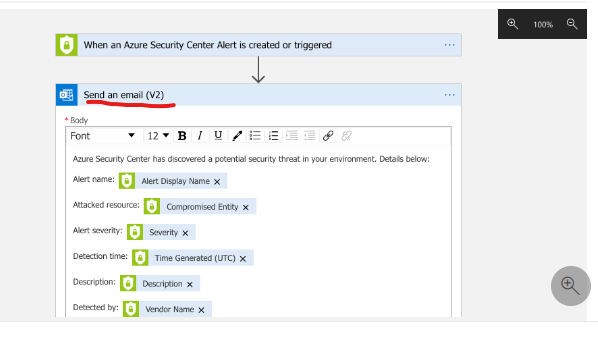
Automating incident response helps boost SOC productivity. Microsoft Sentinel works with Azure Logic Apps to construct event-triggered playbooks. Incident management, enrichment, investigation, and remediation might use this feature. Security orchestration, automation, and response describe these capabilities (SOAR).
Playbooks can use the triggers and actions available in the Logic Apps Microsoft Sentinel connector to communicate with Microsoft Sentinel and the data stored in your workspace’s tables.
Playbooks in Microsoft Sentinel are based on workflows built in Azure Logic Apps.
Run a playbook manually on an incident ( Triggering Email)
Logic App Designer
- Create an automation rule
- Create a playbook
- Add actions to a playbook
- Attach a playbook to an automation rule or an analytics rule to automate threat response
Microsoft Sentinel workspace
In order to successfully deploy the Microsoft Sentinel environment, you will need to build a workspace configuration that satisfies the demands of your security and compliance standards. You will be tasked with establishing a workspace for Log Analytics and configuring the Microsoft Sentinel parameters during the provisioning process.
Microsoft Sentinel uses Azure Monitor Log Analytics as its default logging location.
The Log Analytics Workspace is where Microsoft Sentinel is deployed; therefore, most implementation considerations are about creating it. When building a Log Analytics Workspace, region is the most effective option. Log data will be stored in the region.
Implementation Options
- Single-Tenant with a single Microsoft Sentinel Workspace (Central repository)
- Single-Tenant with regional Microsoft Sentinel Workspaces.
- Multi-Tenant.
Microsoft Defender for Cloud logs can be consumed and used by Microsoft Sentinel if they are in the same workspace. Microsoft Defender for Cloud’s default workspace won’t be available for Microsoft Sentinel.
Workspaces belonging to several tenants can be managed with Azure Lighthouse.
Roles and permissions
Microsoft Sentinel provides built-in Azure RBAC roles for individuals, groups, and services.
- Microsoft Sentinel Reader: can view data, incidents, workbooks, and other Microsoft Sentinel resources.
- Microsoft Sentinel Responder: can, in addition to the above, manage incidents (assign, dismiss, etc.)
- Microsoft Sentinel Contributor: can, in addition to the above, create and edit workbooks, analytics rules, and other Microsoft Sentinel resources.
- Microsoft Sentinel Automation Contributor: allows Microsoft Sentinel to add playbooks to automation rules. It isn’t meant for user accounts.
Type of logs
Each table in a Log Analytics workspace retains data for a certain amount of time before being deleted or archived at a reduced fee
Microsoft Sentinel maintains three primary log kinds, which are as follows:
- Analytics Logs: By default, all tables are in a workspace.
- Basic logs: Retained for 8 days.
- Archive Logs: Archiving keeps less-used data in your workspace for longer and Each table has its own unique retention policy to reduce costs ( stored over 7 years but can not query directly).
KQL is the language used to query log data in the Log Analytics workspace. In Microsoft Sentinel, the query window can be reached from the Logs page. You can run queries, save queries, run saved queries, make a new alert rule, and export data from the query window.
Data retention at the workspace level can be configured from 30 to 730 days (two years) for all workspaces unless they’re using the legacy Free pricing tier
The tables below detail the Microsoft Sentinel features.
| Table | Description |
|---|---|
| SecurityAlert | Contains Alerts Generated from Sentinel Analytical Rules. Also, it could include Alerts created directly from a Sentinel Data Connector |
| SecurityIncident | Alerts can generate Incidents. Incidents are related to Alert(s). |
| ThreatIntelligenceIndicator | Contains user-created or data connector ingested Indicators such as File Hashes, IP Addresses, Domains |
| Watchlist | A Microsoft Sentinel watchlist contains imported data. |
Understand common tables
The following table details the most common tables when importing data into Sentinel via the Data Connectors.
| Table | Description |
|---|---|
| AzureActivity | Entries from the Azure Activity log that provides insight into any subscription-level or management group level events that have occurred in Azure. |
| AzureDiagnostics | Stores resource logs for Azure services that use Azure Diagnostics mode. Resource logs describe the internal operation of Azure resources. |
| AuditLogs | Audit log for Azure Active Directory. Includes system activity information about user and group management, managed applications, and directory activities. |
| CommonSecurityLog | Syslog messages using the Common Event Format (CEF). |
| McasShadowItReporting | Microsoft Cloud App Security logs |
| OfficeActivity | Audit logs for Office 365 tenants collected by Microsoft Sentinel. Including Exchange, SharePoint and Teams logs. |
| SecurityEvent | Security events collected from windows machines by Azure Security Center or Microsoft Sentinel |
| SigninLogs | Azure Activity Directory Sign-in logs |
| Syslog | Syslog events on Linux computers using the Log Analytics agent. |
| Event | Sysmon Events collected from a Windows host. |
| WindowsFirewall | Windows Firewall Events |
Microsoft 365 Defender tables
Raw data from Microsoft 365 Defender solutions can be populated into tables through the Sentinel Data Connector.
| Table name | Description |
|---|---|
| AlertEvidence | Files, IP addresses, URLs, users, or devices associated with alerts |
| CloudAppEvents | Events involving accounts and objects in Office 365 and other cloud apps and services |
| DeviceEvents | Multiple event types, including events triggered by security controls such as Windows Defender Antivirus and exploit protection |
| DeviceFileCertificateInfo | Certificate information of signed files obtained from certificate verification events on endpoints |
| DeviceFileEvents | File creation, modification, and other file system events |
| DeviceImageLoadEvents | DLL loading events |
| DeviceInfo | Machine information, including OS information |
| DeviceLogonEvents | Sign-ins and other authentication events on devices |
| DeviceNetworkEvents | Network connection and related events |
| DeviceNetworkInfo | Network properties of devices, including physical adapters, IP and MAC addresses, as well as connected networks and domains |
| DeviceProcessEvents | Process creation and related events |
| DeviceRegistryEvents | Creation and modification of registry entries |
| EmailEvents | Microsoft 365 email events, including email delivery and blocking events |
| EmailPostDeliveryEvents | Security events that occur post-delivery, after Microsoft 365 has delivered the emails to the recipient mailbox |
| EmailUrlInfo | Information about URLs on emails |
| EmailAttachmentInfo | Information about files attached to Office 365 emails |
| IdentityDirectoryEvents | Events involving an on-premises domain controller running Active Directory (AD). This table covers a range of identity-related events and system events on the domain controller. |
| IdentityLogonEvents | Authentication events on Active Directory and Microsoft online services |
| IdentityQueryEvents | Queries for Active Directory objects, such as users, groups, devices, and domains |
Watchlists – Response
Microsoft Sentinel provides a table for storing list data that can be queried using Kusto Query Language (KQL). Microsoft Sentinel’s Watchlists page gives administrative tools for maintaining the lists.
Using Microsoft Sentinel watchlists, you can get information from other places and match it to things that have happened in your Microsoft Sentinel environment.
Watchlists can then be used in your search, detection rules, threat hunting, and response playbooks. Your Microsoft Sentinel workspace will keep your watchlists as cached name-value pairs for fast querying and low latency.
- Investigating risks and responding to incidents quickly using the rapid input of IP addresses, file hashes, and other data from CSV files.
- Importing business data as a watchlist
- Reducing alert fatigue
- Enriching event data
- File uploads are currently limited to files of up to 3.8 MB in size.
- _GetWatchlist(‘HighValueMachines’) ( KQL)
Log analytics ingestion SLA is five minutes. During this five-minute span, Log Analytics may show both deleted and regenerated watchlists.
Threat intelligence – Indicators of Compromise (IoCs)
The administration choices necessary to keep the indications up to date can be found on the Threat intelligence page of Microsoft Sentinel.
Threat indicators are delivered to you by threat intelligence providers as well as by your threat-hunting team. Numerous components inside Microsoft Sentinel are able to make use of the IP addresses, domains, and file hashes that are contained within the Indicators.
The indicators from the threat intelligence providers are automatically imported into the workspace using connectors
Security solutions and automation leverage tactical threat intelligence to protect and identify threats. Microsoft Sentinel detects, responds, and provides CTI context for malicious cyber activity.
Threat Tagging
Threat indicators can be grouped by tagging them. You might tag indicators pertaining to a specific occurrence or threats from a known actor or attack campaign. You can tag threat indicators individually or all at once. Since tagging is free-form, threat indicator tags should have conventional names
The indicators reside in the ThreatIntelligenceIndicator table
Data connectors
In order to collect log data, you will need to connect the various sources of data using Microsoft Sentinel Connectors.
Configuring data connectors sends data to Microsoft Sentinel. The data connectors are for Microsoft 365, Azure, and third-party services.
The connector does not install Workbooks and Analytics Templates.
Logstash plugin
Microsoft Sentinel’s output plugin for Logstash lets you transmit any log to your Log Analytics workspace in Microsoft Sentinel. Using the output plugin, logs are written to a custom table.
Common Event Format
Format built on top of Syslog messages that enables event interoperability across platforms. CommonSecurityLog primarily table stores data ingested by the Common event format connector.
Syslog connector
Syslog is a standard Linux protocol for logging system events. Messages generated by applications can either be saved locally or sent to a Syslog collector.
The CommonSecurityLog table parses log data, making CEF the best option. The Syslog table’s SyslogMessage column contains the raw log message with unparsed field.
Azure Active Directory connector: writes to the Sign-On logs and Audit logs.
Office 365 connector: writes to the OfficeActivity table.
Azure Active Directory Identity Protection Connector : writes to the SecurityAlert table
Microsoft 365 Defender connector: SecurityAlert
Microsoft 365 Defender Connector
Microsoft 365 Defender connector with incident integration streams all Microsoft 365 Defender incidents and alerts into Microsoft Sentinel and syncs them between portals. Microsoft 365 Defender incidents include alerts, entities, and other relevant data. Microsoft Defender for Endpoint, Identity, Office 365, and Cloud Apps alerts are bundled together and augmented.
Microsoft Defender for Cloud connector
Microsoft Defender for Cloud is a security management tool for Azure, hybrid, and multi-cloud workloads that detects and responds to threats. This connector lets you feed security alerts from Microsoft Defender for Cloud to Microsoft Sentinel. Then you may query Defender data in workbooks, investigate incidents, and respond to alarms.
Microsoft Defender for IoT
Connect Microsoft Defender for IoT alerts to Microsoft Sentinel to analyze IoT security. Out-of-the-box alert analytics and data include alert trends, top alerts, and severity breakdowns. You can also see your IoT hubs’ top and severity-based recommendations.
Microsoft Defender legacy connectors
Instead of legacy connectors, utilize Microsoft 365 Defender.
Windows Hosts
Windows hosts security events connector options to stream events from Windows devices to Microsoft Sentinel.
There are two agents available:
- Windows Security Events via AMA Connector ( Data Collection Rules (DCRs) )
- Security Events via Legacy Agent Connector ( Windows Forwarded Events connector)
Collect Sysmon event logs
System Monitor (Sysmon) is a device driver and Windows system service that monitors and logs system activities to the Windows event log after installation. It gives precise information about process creations, network connections, and file creation time changes. You may spot malicious or abnormal activity and understand how intruders and malware operate on your network by collecting and analyzing its events with Windows Event Collection or SIEM agents.
Azure Sentinel Livestream
Livestream lets you run queries that refresh every 30 seconds and notifies you of any new results.
Hunting streaming lets you establish interactive sessions to test new queries, receive notifications when a match is found, and begin investigations if needed. Log Analytics queries can produce livestream sessions quickly.
Workbooks are given to analysts and SOC managers so they can use the Sentinel data to make interactive views and reports.
Notebooks should be a big part of what the security team does every day, especially if they use Microsoft Sentinel as their SIEM.
Entity tags
Three types of Defender for Identity entity tags:
Sensitive tags: Used to identify high-value assets. ( Users, Devices, and Groups -Defender for Identity)
Honeytoken tags: Used as traps for malicious actors. ( Users and Devices)
Exchange server tags.Exchange servers as sensitive assets. ( Users and Devices)
Govern Discovered Apps
Select the app, Sanctioning/unsanctioning an app, Blocking apps with built-in streams, Block apps by exporting a block script, Blocking unsupported streams, and Run the script on the source appliance.
Defender for Cloud triggers
When a Microsoft Defender for Cloud Recommendation is created or triggered: To track changes to recommendations.
When a Defender for Cloud Alert is created or triggered: Alerts with the severity levels that interest you.
When a Defender for Cloud regulatory compliance assessment is created or triggered: Regulatory compliance assessments.