Microsoft Sentinel Analytics is an intelligent tool that can be utilized by your business to identify potential threats and vulnerabilities inside business system components.
Microsoft Sentinel to help the SecOps team identify and stop cyberattacks.
Microsoft Sentinel Analytics
Microsoft Sentinel Analytics helps you detect, investigate, and remediate cybersecurity threats.
Analyze historical data from workstations, servers, networking devices, firewalls, intrusion protection, sensors, and more. Microsoft Sentinel Analytics finds relationships and anomalies in several data sources.
Analytics rules can alert you to known malicious actor attack methods. These rules can help your SOC detect security events in your environment quickly.
Analytics rules
The right analytics rule can reveal an attack’s origin, compromised resources, data loss, and timeline.
Analytics rules can also generate custom alerts based on attack indicators. These indicators can detect ongoing attacks in real-time.
Common security analytics use cases include:
- Identification of compromised accounts
- User behavior analysis to detect potentially suspicious patterns
- Network traffic analysis to locate trends indicating potential attacks
- Detection of data exfiltration by attackers
- Detection of insider threats
- Investigation of incidents
- Threat hunting
Real-world adversary tactics and approaches are available worldwide in MITRE ATT&CK. The business industry, government, and cybersecurity product and service communities construct threat models and methodologies using the ATT&CK knowledge base.
The Analytics home page has three main parts:
- The number of rules in use is displayed in the header bar.
- Rules and templates: Microsoft preloads rule templates from the Microsoft Sentinel GitHub repository.
- The details pane describes each detection template and rule.
Types of analytics rules
Five analytics rules exist:
- Anomaly: Anomaly alerts are informational and identify anomalous behaviors.
- Fusion: Fusion alerts identify suspicious activities at various stages of the cyber kill chain (technique)
- Microsoft security: Microsoft security solutions connected to Microsoft Sentinel automatically create incidents from all service alerts.
- Machine learning (ML) behavior analytics: Microsoft Sentinel Analytics includes built-in machine learning behavior analytics rules.
- Scheduled alerts: Kusto Query Language (KQL) lets you filter security events using your own expression and schedule the rule to run.
Attackers exploit the cyber kill chain to enter an organization’s networks and systems.
Fusion and ML behavior analytics rules, Microsoft doesn’t provide any editable information
Predefined rule template
Security Orchestration and the Automation and Response (SOAR)
SIEM solutions store and analyze system logs, events, and alerts. Configure these solutions to alert themselves.
SOAR solutions support the remediation of vulnerabilities and the overall automation of security processes.
Microsoft Sentinel Playbook – Response to an alert
A Microsoft Sentinel playbook is a collection of security procedures that you can run in response to alerts.
Microsoft Sentinel security playbooks respond to alerts. Security playbooks are Azure Logic App-based alert-response routines. These security playbooks can be run manually or automatically by an alert.
Azure Logic Apps – Alerts Automation
Azure Logic Apps automate business operations. Logic Apps Designer lets you sequence prebuilt components. Code view lets you write your automated procedure in JSON.
Logic Apps Connector – API Connection
Logic Apps and Microsoft Sentinel connectors are different.
Microsoft Sentinel data connectors connect Microsoft security products and security ecosystems for non-Microsoft solutions.
A Logic Apps connector provides an API connection for an external service and integrates events, data, and actions across apps, services, systems, protocols, and platforms.
A trigger is an event that occurs when a specific set of conditions is satisfied
Actions run when a trigger activates . An action is an operation that performs a task in the Logic Apps workflow.
Microsoft Sentinel Logic Apps connector
The Microsoft Sentinel Logic Apps connector is utilized by a Microsoft Sentinel playbook. It offers the triggers and actions that can initiate playbook execution and execute predefined activities.
Currently, there are two triggers from Microsoft Sentinel Logic Apps connector:
- When a response to a Microsoft Sentinel alert is triggered
- When the Microsoft Sentinel incident creation rule is triggered
Incident management
Incident management encompasses the entire incident investigation process, from initiation to in-depth investigation to resolution.
Data connectors > Events > Analytic rules > Alerts > Incidents
Incident evidence
Incident evidence includes security event information and linked Microsoft Sentinel assets that identify threats. Evidence shows Microsoft Sentinel’s threat detection. It directs you to resources for incident awareness.
Bookmarks
You may find events to follow or investigate later while examining an incident. Bookmarking events in Log Analytics preserves queries. Notes and tags can help with threat-hunting afterward. Your team has bookmarks.
Incident entities
An entity refers to a network or user resource involved with an event.
User account (Account), Host IP address (IP), Malware, File, Process, Cloud application, (CloudApplication), Domain name (DNS), Azure resource, File (FileHash), Registry key, Registry value, Security group, URL, IoT device, Mailbox, Mail cluster, Mail message, Submission mail
Entity Insights
The entity page’s insights provide hosts’ and users’ security statistics in tabular and chart form.
The insights are based on the following data types
- Syslog
- SecurityEvent
- Audit Logs
- Sign-in Logs
- Office Activity
- BehaviorAnalytics (UEBA)
Behavioral analytics
Identifying internal threats, such as compromised entities or malicious insiders, has always been a time-consuming and laborious task.
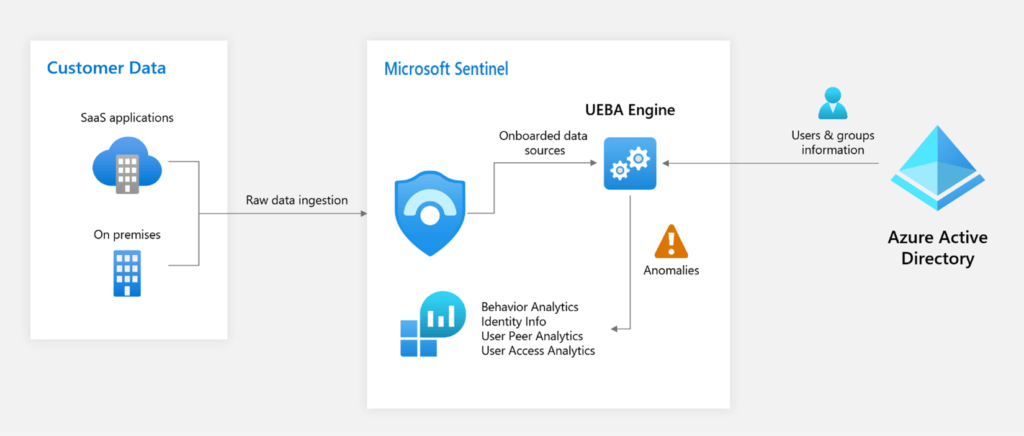
Insights display information from the Entity behavior data.
The Incident Investigation Graph includes an option for Insights
Security-driven analytics
Microsoft Sentinel uses Gartner’s “outside-in” UEBA concept and three frames of reference
Use cases: Microsoft Sentinel prioritizes relevant attack routes and scenarios based on security research linked with the MITRE ATT&CK structure of tactics, techniques, and subtechniques. Victims, perpetrators, and kill chain pivot points are prioritized. Microsoft Sentinel concentrates on each data source’s most valuable logs.
Data Sources: While Microsoft Sentinel’s primary focus is on Azure data sources, it carefully selects third-party data sources to give information about potential threats that is relevant to our use cases.
Analytics: Microsoft Sentinel detects anomalies using machine learning (ML) techniques and provides contextual enrichments.
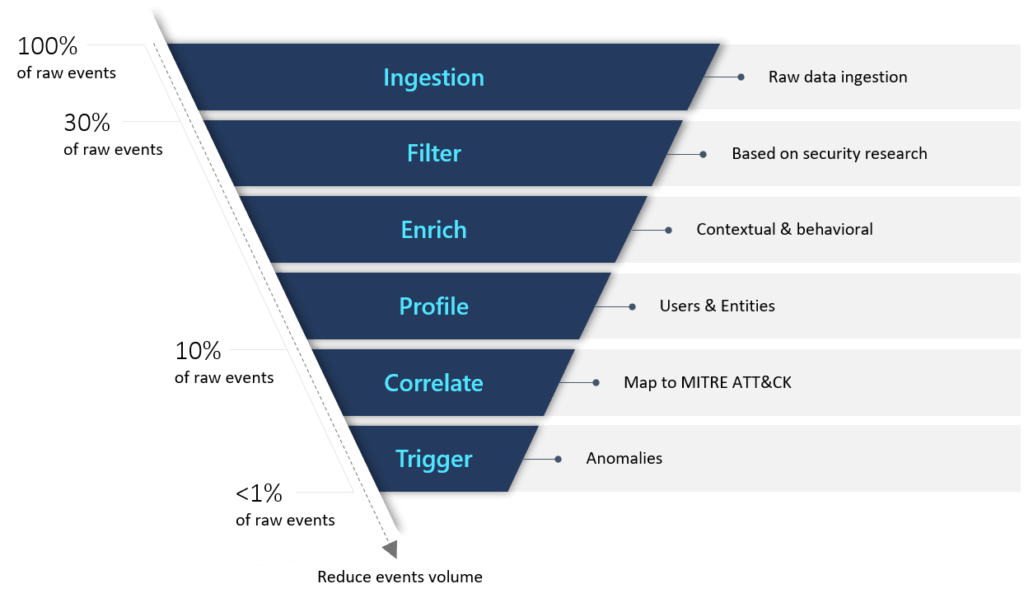
Scoring “Investigation Priority Score” ranks each activity. Based on user and peer behavior, the score predicts a user’s activity. Abnormal activities score highest (on a scale of 0-10).
Data normalization
The Advanced Security Information Model (ASIM) is a layer that is located between these diverse sources and the user. ASIM follows the robustness principle: “Be strict in what you send, be flexible in what you accept”
Manage content in Microsoft Sentinel
- Content hub: – Microsoft Sentinel solutions are bundles of content or API connections that complete a product, domain, or industry vertical scenario.
- Repositories: -Central repositories automate Microsoft Sentinel deployment and administration.
- Community: GitHub repo at https://github.com/Azure/Azure-Sentinel
Threat hunting concepts in Microsoft Sentinel
People define “threat hunting” differently. The most typical meaning is that you’re actively looking for threats or activities you haven’t seen before. Threat hunting differs from incident response and alert triage by being “not previously detected”.
Proactive hunts
Why go on a proactive hunt? The danger of a more severe compromise is a concern while you search for “not previously discovered” threats.
Develop a hypothesis
Keep it achievable, Keep the scope narrow, Keep it time-bound, Keep it useful and efficient, and Keep it related to the threat model that you are defending against
MITRE ATT&CK framework
MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) is a framework, set of data matrices, and assessment tool made by MITRE Corporation to help organizations understand their security readiness and find vulnerabilities in their defenses.
Microsoft Sentinel uses the MITRE ATT&CK framework to categorize and order queries by tactics
Tactics include Reference to microsoft.com
- Initial access. Tactics that the adversary uses to gain entry to a network, by exploiting vulnerabilities or configuration weaknesses in public-facing systems. An example is targeted spear-phishing.
- Execution. Tactics that result in an adversary running their code on a target system. For example, a malicious hacker might run a PowerShell script to download more attacker tools and/or scan other systems.
- Persistence. Tactics that allow an adversary to maintain access to a target system, even after restarts and credential change. An example of a persistence technique is an attacker who creates a scheduled task that runs their code at a specific time or on restart.
- Privilege escalation. Tactics that an adversary uses to gain higher-level privileges on a system, such as a local administrator or root.
- Defense evasion. Tactics that attackers use to avoid detection. Evasion tactics include hiding malicious code within trusted processes and folders, encrypting or obfuscating adversary code, or disabling security software.
- Credential access. Tactics deployed on systems and networks to steal usernames and credentials for reuse.
- Discovery. Tactics that adversaries use to obtain information about systems and networks that they want to exploit or use for their tactical advantage.
- Lateral movement. Tactics that allow an attacker to move from one system to another within a network. Common techniques include pass-the-hash methods of authenticating users and abuse of the Remote Desktop Protocol.
- Collection. Tactics that an adversary uses to gather and consolidate the information they were targeting as part of their objectives.
- Command and control. Tactics that an attacker uses to communicate with a system under their control. One example is an attacker communicating with a system over an uncommon or high-numbered port to evade detection by security appliances or proxies.
- Exfiltration. Tactics are used to move data from the compromised network to a system or network that’s fully under the control of the attacker.
- Impact. Tactics that an attacker uses to affect the availability of systems, networks, and data. Methods in this category include denial-of-service attacks and disk-wiping or data-wiping software.
Hunt with a Search Job
One of the primary activities of a security team is to search logs for specific events.
Search results remain in a search results table that has a *_SRCH suffix.
Supported : Analytics logs and Basic logs
Limitations of a search job
Before you start a search job, be aware of the following limitations:
- Optimized to query one table at a time.
- The search date range is up to one year.
- Supports long-running searches up to a 24-hour time-out.
- Results are limited to one million records in the record set.
- Concurrent execution is limited to five search jobs per workspace.
- Limited to 100 search results tables per workspace.
- Limited to 100 search job executions per day per workspace.
Restore historical data
A restored log table is available in a new table that has a *_RST suffix.
Limitations of log restore
Before you start to restore an archived log table, be aware of the following limitations:
- Restore data for a minimum of two days.
- Restore data more than 14 days old.
- Restore up to 60 TB.
- Restore is limited to one active restore per table.
- Restore up to four archived tables per workspace per week.
- Limited to two concurrent restore jobs per workspace.
Hunt for threats using notebooks in Microsoft Sentinel
Microsoft Sentinel notebooks can be used for advanced hunting.
After developing your hunting hypothesis, use a Jupyter notebook to incorporate machine learning frameworks, complex visualizations, and external data to discover malicious behavior patterns.
The Azure portal and Microsoft Sentinel tools access this data store using a standard API. Python and PowerShell can also use the API.
Two libraries ease API access: Kqlmagic and msticpy
Kqlmagic
The Kqlmagic library provides an easy-to-implement API wrapper to run KQL queries.
msticpy
Microsoft Threat Intelligence Python Security Tools is a set of Python tools intended to be used for security investigations and hunting.
Notebooks
- Jupyter Notebooks let you create and share documents with live code, equations, visualizations, and explanations.
- Numerical simulation, statistical modeling, machine learning, data cleaning and transformation, and more are used. Microsoft Sentinel data is more useful with Jupyter.
- It offers full programmability and a large library for machine learning, visualization, and data analysis. Jupyter is handy for security hunting due to these features.
- Several notebooks employ msticpy. Msticpy tools are specifically for hunting and investigative notebooks.