Azure Active Directory (Azure AD) is an IAM (Identity and Access Management) service hosted in the cloud. This solution facilitates your company’s use of the Internet and external resources, including Microsoft 365, the corporate intranet, Custom cloud apps, and a large number of other SaaS applications.
This strategy is taken to a whole new level by Azure Active Directory, which offers businesses an Identity as a Service (IDaaS) solution that can be used for any of their applications, regardless of whether they are cloud-based or run locally.
Azure AD is intended for:
- IT administrators: Control app and resource access depending on business needs.
- App developers: Single sign-on functionality.
- Users: self-service password reset, identity management
- Online service subscribers: Microsoft Office 365 and Azure applications can authenticate via Azure AD.
Authentication, Single sign-on, Application management and Device management
On-premises AD Connects to Azure AD:
You can integrate on-premises Active Directory with Azure Active Directory by utilizing Azure AD Connect. Users’ identities in both on-premises Active Directory and Azure AD may be kept in sync with the help of Azure AD Connect. With Azure AD Connect, you can use capabilities like single sign-on (SSO), multi-factor authentication (MFA), and self-service password reset (SSR) with either identity provider.
Azure Active Directory Domain Services
When using Azure, applications, services, and virtual machines (VMs) that connect to a managed domain are then able to take advantage of standard Azure AD DS features. These features include domain join, group policy, LDAP, and Kerberos/NTLM authentication.
Azure AD Privileged Identity Management: PIM is a service that manages, controls, and monitors access to Azure resources. These resources include Azure AD, Azure, Microsoft 365, and Microsoft Intune.
Azure AD Identity Protection: Detects risks ( Access log, IP location, malware, virus, etc.) and investigates risks ( Review and action lists )
Azure Authentication Methods
Azure Internal identities
- Single Sign-on: lets users log into multiple apps and sites with one set of credentials.
- Multifactor Authentication: uses various types of credentials to validate a user’s identity for login.
- Passwordless Authentication: User identification without a password
- FIDO2 security keys: Fast IDentity Online- (FIDO): unfishable standards-based passwordless authentication method
Azure external identities
- Business to business (B2B): External users can use their preferred identity to sign in to your applications. ( Simply Guest user)
- B2B direct connect: Mutual authentication with another Azure AD domain
- Azure AD business-to-consumer (B2C): Azure AD B2C identifies and authenticates consumers and customers.
Azure Conditional Access
Azure Active Directory employs Conditional Access to grant or revoke access to resources based on user identities and other signals.
- Signal: location, device, or app the user is attempting to use.
- Decision: Authorize or deny access based on regular or irregular location.
- Enforcement: either grant access or request a second authentication factor.
Azure Role-Based Access Control
Only issue permissions that are truly necessary for a given task, as stated by the concept of least privilege. Azure has standard roles that define access to frequently used cloud resources to meet the latest privilege permissions. If you need to, you can also build custom roles to meet your business needs.
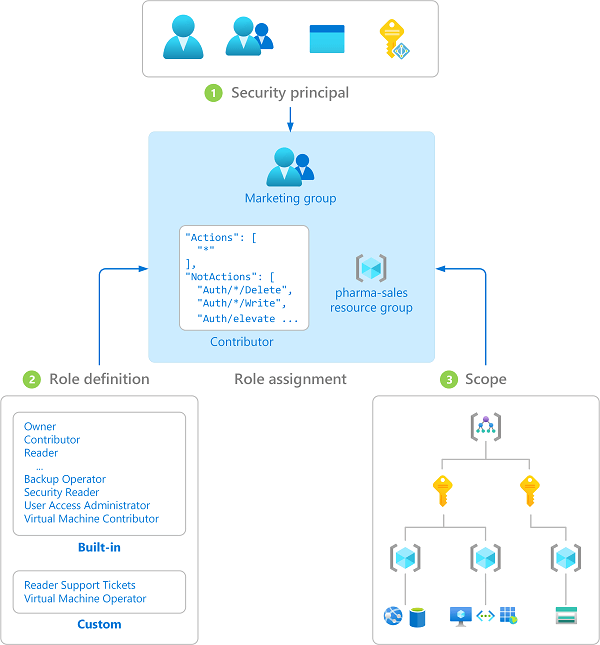
Role assignments include a security principal, role definition, and scope.
A role assignment attaches a role description to a user, group, service principal, or managed identity to give access. Role assignments allow and withdraw access.
Security principal: Belongs to user, group, service principal, or managed identity.
Role definition: Action includes read, write, and delete.
Scope: management group, subscription, resource group, or resource.
Defense-in-depth
Those who are not permitted to access the information should be prevented from doing so in order to avoid the information being stolen.
Layers of defense-in-depth
- Physical security: securing data center buildings and hardware ( Ex: Security guard and Entry )
- Identity and access: securing identities, limiting access, and logging sign-ins and changes. ( Ex: Control access, SSO, access logs )
- Perimeter: Network-based resource attacks ) e.g.: DDoS protection, Firewall services )
- Network: limiting all of your resources’ network connections to only what is required to perform tasks (e.g.: Inbound and Outbound access – Internet )
- Compute: keep systems patched and secure access to computer resources
- Application: Protecting and distributing secure software code makes apps secure by default ( Ex: Storininformation at aon secure level )
- Data: CIA: data confidentiality, integrity, and availability – core principle to ensure data
Microsoft Defender for Cloud
Cloud security posture management (CSPM) and cloud workload protection (CWP)
Support : Azure, on-premises, Google Cloud and Amazon AWS
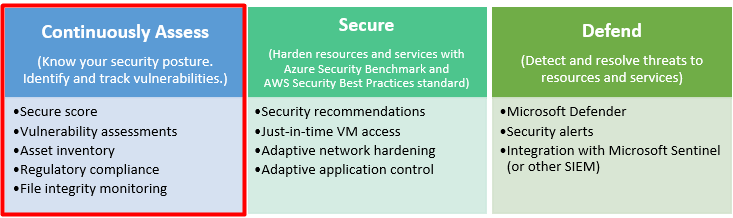
- Continuously assess – Know your security posture. Identify and track vulnerabilities.
- Secure – Harden resources and services with the Azure Security Benchmark.
- Defend – Detect and resolve threats to resources, workloads, and services.
Advanced threat protection features :
includes virtual machines, SQL databases, containers, web apps, and your network
Just-in-time access secures VM management ports, and Adaptive application controls use allow lists to secure execution.