Virtual machine storage virtual machines in Azure use disks as a place to store the operating system, applications, and data.
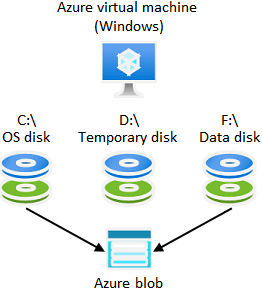
Operating system disk Each virtual machine has an OS file. When creating a virtual machine, the OS disk’s pre-installed OS is chosen. The OS disc is a SATA drive and is named C: by default.
Temporary disk During virtual machine redeployment or repair, temporary disc data may be lost. Data on the temporary disc should survive a virtual machine reboot. Data may be lost if the host changes.
- On Windows virtual machines, the temporary disk is labeled as the
D:drive by default. This drive is used for storing the pagefile.sys file. - On Linux virtual machines, the temporary disk is typically
/dev/sdb. This disk is formatted and mounted to/mntby the Azure Linux Agent.
Data disks A data disc is a managed disc that’s connected to a virtual machine and used to store application data or other data you need to keep. Data discs are set up as SCSI drives and given a letter that you pick. Depending on the size of a virtual machine, you can attach a certain number of data discs and use a certain type of storage to hold those discs.
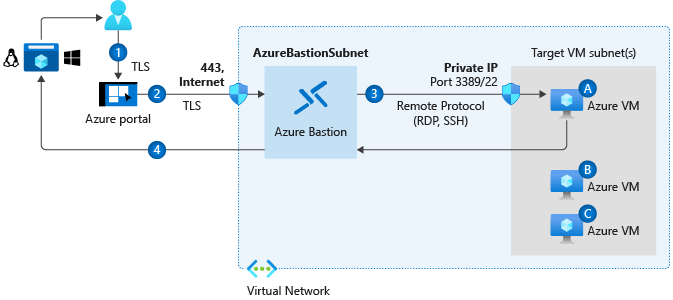
Connect to virtual machines
Azure virtual servers can be accessed in various ways. Connecting Windows and Linux devices using Azure Bastion is possible through the Azure portal. Azure virtual servers can be connected to SSH, RDP, Cloud Shell, and Azure Bastion using the following diagram.
Virtual machines extensions
Azure virtual machine extensions are small apps for post-deployment setup and automation. A virtual machine needs software installation, anti-virus protection, or a configuration script. Virtual machine extensions can perform these tasks. Extensions manage virtual devices.
Custom Script Extensions can automate virtual machine modification after initial setup. Your script extension can stop the virtual machine or load software. Complex scripts execute multiple tasks.
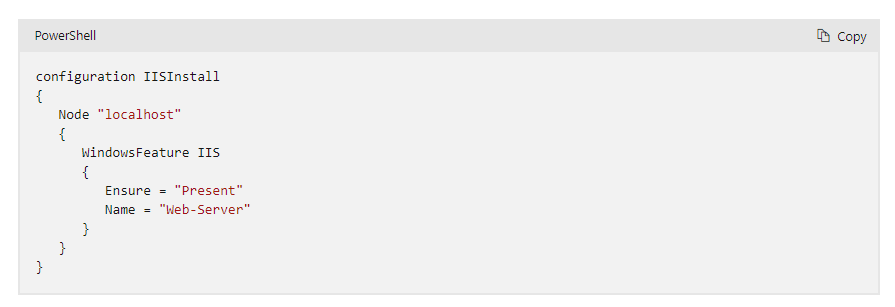
Desired State Configuration
Windows PowerShell’s Desired State Configuration is an administration framework. Using Desired State Configuration, you can control the infrastructure in which your software services operate and how they are deployed. The platform also lets you keep and manage configurations that have already been set up.
Implement Azure App Service
You can develop websites, mobile backends, and web APIs for any platform or device with the help of Azure App Service because it brings together everything you need to do so. Applications are able to operate smoothly and easily scale in environments based on either Windows or Linux.

Explore continuous integration and deployment
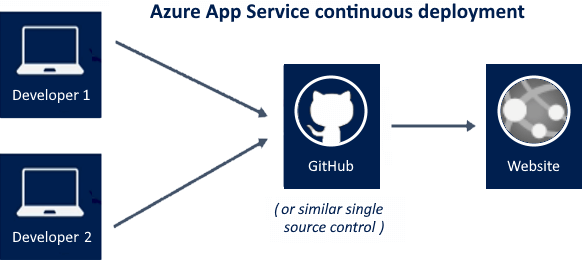
- Automated deployment (continuous integration) releases new features and bug fixes quickly and repetitively with minimal user effect. Azure automates release from multiple sources.
- Azure DevOps: Build your code in Azure DevOps (formerly Visual Studio Team Services), run the tests, create a release, and push it to an Azure web app.
- GitHub: Azure automates GitHub release. When you connect your GitHub repository to Azure for automated deployment, changes to your production branch are immediately deployed.
- Bitbucket: Bitbucket can handle deployment like GitHub.
- Manual deployment sending code has several options:
- Git: App Service Web Apps provide a remote store Git URL. Pushing to the remote source deploys your app.
- CLI: Your app is packaged and deployed by the command-line interface’s web app up command. A new App Service web app can be deployed.
- Visual Studio: The App Service launch wizard in Visual Studio guides you through the process.
- FTP/S: Many hosting environments, including App Service, use FTP or FTPS to send code.
Deployment slots
When you deploy your web app, web app on Linux, mobile backend, or API app to Azure App Service, you have the option of using a distinct deployment slot rather than the production slot that is pre-configured by default.
App Service for app security
Allow Anonymous requests (no action) to Authorize unauthenticated traffic with your application code. In HTTP headers, the App Service passes authentication details for authenticated requests. Anonymous requests are more flexible with this tool. You can offer numerous sign-in providers to users with this feature.
Allow only authenticated requests Redirect anonymous queries to /.auth/login/. Log in with. Native mobile apps reply HTTP 401 Unauthorized for anonymous requests. This feature eliminates the app verification code.
Logging and tracing Log files show authentication and permission. Look in your application logs for data on unexpected authentication errors. Failed request tracing shows how the security module affected a lost request. Check the trace files for any mention of a module with the name EasyAuthModule 32/64.
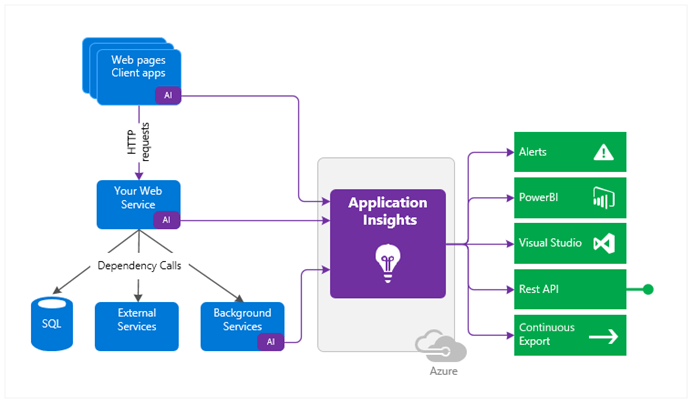
Azure Application Insights
Azure Monitor includes a function called Azure Application Insights that gives you the ability to monitor your live applications. Application Insights can be integrated with your App Service configuration to carry out automated performance anomaly detection in your applications.
Azure Automation State Configuration
You use Azure Automation State Configuration to make sure that the virtual machines (VMs) in a cluster area are in a consistent state, with the same software installed and the same configurations.
It’s hard and error-prone to manually configure your service hosts. PowerShell DSC helps Azure Automation State Configuration solve these issues. Your DSC artifacts and process are directly managed by it.
Pull servers are baked into Azure Automation State Configuration. You can target nodes to autonomously receive configurations from this pull server, conform to the desired state, and report compliance. Target virtual or physical Windows or Linux devices in the cloud or on-premises.
By setting Azure Automation State Configuration to send Azure Monitor logs, you can check node compliance.