Email, collaboration, identity, device, and app threats are protected, detected, investigated, and responded to in the Microsoft 365 Defender portal.
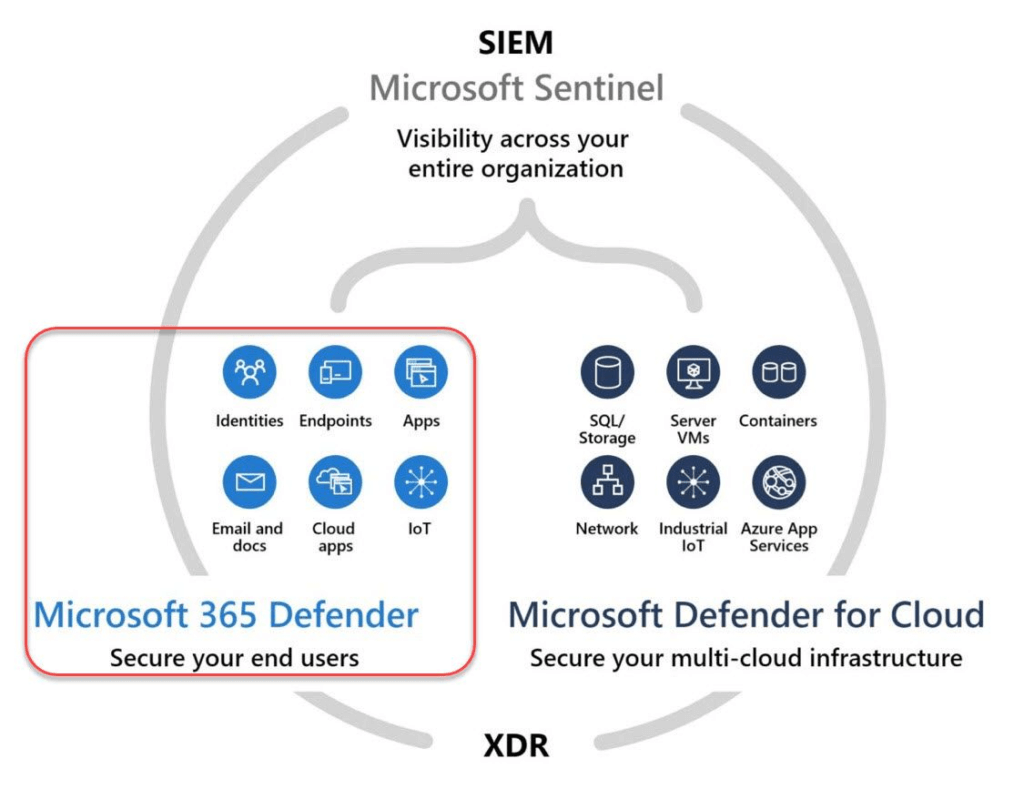
Microsoft 365 Defender, a comprehensive pre- and post-breach enterprise defense suite package, natively integrates detection, prevention, investigation, and response across endpoints, identities, email, and applications to guard against sophisticated cyberattacks.
The term “security posture” refers to the entire level of an organization’s readiness with regard to cybersecurity.
Risks: Cybersecurity risk is the potential for harm to an organization’s reputation, critical assets, and information resulting from a cyber attack or breach.
Vulnerability: A vulnerability is a weakness, flaw, or error that attackers can exploit. Vulnerabilities allow attackers to get unauthorized access.
Events: This is an observed change in the behavior of a normally functioning device, system, process, or user. Almost all logs can be thought of as events.
Action + Target
Incident: No matter how you define “problem,” an incident is something that shows there is a problem. It comes from an event, but it also has a layer of meaning on top of it. This is an event that negatively affects the company’s business activity.
Attacker + ATTACK + objective
Alert: A unique, urgent notification concerning a specific event (or combination of events) is delivered to responsible parties to prompt action. A SIEM, firewall, or DLP must notify you of an alert based on your security policies. An alert may pertain to multiple events.
Attack: Attempt to destroy, expose, alter, disable, steal, or gain unauthorized access to or make unauthorized use of an asset.
Tools + Vulnerability + EVENT + Unauthorized result
Threat: A threat is anything that has the potential to cause an incident. People, weather, machines, etc.
Microsoft 365 Defender
Microsoft’s Extended Detection and Response (XDR) solution.
Microsoft 365 Defender will immediately begin taking measures to either stop the attack or prevent further damage.
- Identity: On-premises Active Directory.
- Azure Active Directory (Azure AD) Identity Protection: Azure AD
- Endpoint: Devices in your organization.
- Office 365: Protect email and Office 365 resources.
- Cloud Apps: Cross-SaaS and PaaS solution.
- Vulnerability Management: Fix critical vulnerabilities, Misconfigurations and Insider Risk Management.
- Microsoft Defender for Cloud: Protection for cloud and on-premises Azure and non-Azure workloads.
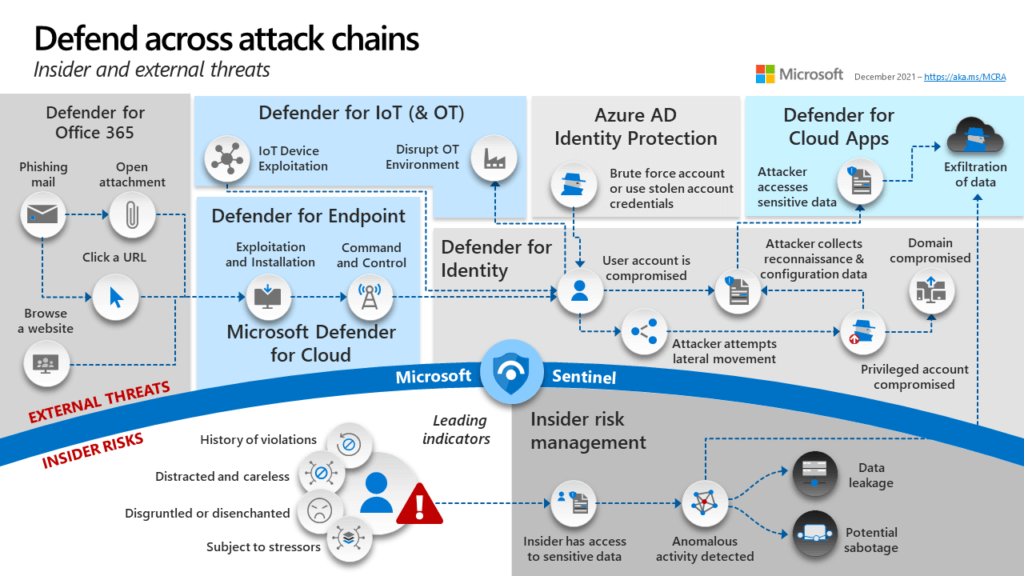
Extended Detection & Response (XDR)
XDR analyzes data from email, endpoints, servers, cloud workloads, and networks to reveal advanced threats. Analyze, prioritize, hunt, and remediate threats to prevent data loss and security breaches.
Microsoft Defender for Endpoint
Microsoft Defender for Endpoint helps enterprise networks detect, analyze, and respond to advanced attacks.
- Endpoint behavioral sensors: These sensors capture and interpret behavioral signals from Windows 10 and 11 and deliver them to your private, isolated, cloud instance of Microsoft Defender for Endpoint.
- Cloud security analytics: Behavioral signals are turned into insights, detections, and recommended solutions to advanced threats using big data, device learning, and unique Microsoft optics throughout the Windows ecosystem, enterprise cloud products (including Office 365), and internet assets.
- Threat intelligence: Defender for Endpoint uses threat intelligence from Microsoft hunters, security teams, and partners to identify attacker tools, techniques, and procedures in sensor data and create alarms.
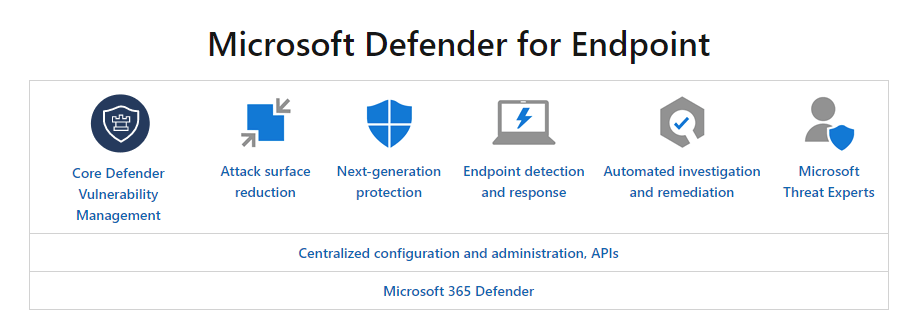
- Microsoft Defender for Endpoints Key characteristics: Alerts, Events, Hunting, Actions, Reporting, Security Analytics, Threat & Vulnerability management
- Endpoint events: Threat & Vulnerability Management, Attack Surface reduction, Exploit protection, Hardware-based isolation, Application control, Network protection, Firewall, Browser protection, Next -gen Av Protection, EDR behavioral sensors, EDR response controller, Update services
- Endpoint output: Visibility, Reporting, Threat & vulnerability, Investigation, hunting, singal exchange, Automated Investigation & response, security analytics, event correlation, and detections.
Built-in, real-time, cloud-powered threat and vulnerability management is fully integrated with the Microsoft endpoint security stack, the Microsoft Intelligent Security Graph, and the application analytics knowledge base. It integrates with Microsoft Intune and Microsoft Endpoint Manager to create security tasks and tickets.
Attack surface reduction
The attack surface reduction capabilities ensure optimal configuration settings and exploit mitigation.
- Hardware-based isolation protects and validates system integrity throughout startup and operation using local and remote authentication. Microsoft Edge container isolation protects the host OS from malicious websites.
- Application control moves from the traditional application trust model where all apps are trusted by default to one where applications must earn trust to run.
- Exploit protection mitigates your organization’s apps individually and collectively.
- Network protection enhances Microsoft Defender SmartScreen in Microsoft Edge’s malware and social engineering protection to network traffic and connection on your organization’s devices.
- Controlled folder access helps prevent file-encrypting ransomware and other malicious software from modifying crucial system folders.
- Attack surface reduction reduces your apps’ attack surface with clever rules that block Office, script, and email-based malware.
- Network firewall host-based, two-way network traffic filtering stops unauthorized network traffic from entering or leaving the local device.
Manage incidents
In order to evaluate possible threats, Microsoft 365 Defender offers a site that is purpose-built and can compare threats from different domains. When a suspicious activity or an event is detected on your network, associated alerts are generated, which are used to produce incidents. Data from individual warnings can be used to piece together information about an ongoing attack. To penetrate a system, however, attackers frequently use a wide variety of channels and methods.
- Alerts: Origin ( Source ) of the alerts.
- Devices: Devices that generate incident alerts.
- Users: locating the users.
- Mailboxes: Investigate incident-related mailboxes.
- Apps: Investigate incident-related apps.
- Investigations: Select Investigations to view this incident’s alert-triggered automatic investigations. Remediation or analyst approval will follow investigations.
- Evidence and Responses: Proactively evaluates all supported events and suspicious entities in alerts, giving you autoresponse and information on essential files, processes, services, emails, and more. This allows incident threats to be identified and blocked immediately.
- Graph: Represents visual threats information.
Severity
- High (Red): Advanced persistent threats (APT).
- Medium (Orange): Originating from endpoint detection and response post-breach behavior but part of PT (Advanced Persistent Threats).
- Low (Yellow): Prevalent malware not part of APT (Advanced Persistent Threats).
- Informational (Grey): Don’t harm the network but promote organizational security awareness input.
Automated Investigation
- Full: Remediate threats automatically (also referred to as full automation).
- Semi: Require approval for any remediation (also referred to as semi-automation).
- Semi: Require approval for core folders (windows) remediation (also a type of semi-automation).
- Semi: Require approval for non-temp folder remediation (also a type of semi-automation).
Explore advanced hunting
Advanced hunting is a query-based technique for finding threats that give you access to up to 30 days’ worth of raw data for investigation.
Event or Activity Data: Populates alert, security, system, and routine assessment tables.
Entity Data: Populates users and devices into tables and fresh data is updated every 15 minutes.
Time information in advanced hunting is in the UTC zone.
Microsoft Secure Score
Products Available
- Microsoft 365 (including Exchange Online)
- Azure Active Directory
- Microsoft Defender for Endpoint
- Microsoft Defender for Identity
- Defender for Cloud Apps
- Microsoft Teams
Analyze threat analytics
High-impact risks are the most dangerous, while high-exposure dangers put your assets at risk. Threat analytics can tell your security operations team about ongoing attacks.
Threat analytics dashboard highlights below
- Latest threats: shows the latest threat reports and current and resolved alerts.
- High-impact threats: shows the high-impact threat reports and current and resolved alerts.
- Highest exposure: Shows the high-exposure threat list and how extensive the threat is and how many devices are vulnerable to it.
Threat tags: Reports related to ransomware
Report types: Reports that cover tools and techniques.
Filters: specific threat tag or report type
Each threat report has threat tags from Microsoft Threat Intelligence.
Four threat tags are now available:
- Ransomware
- Phishing
- Vulnerability
- Activity group
Microsoft Defender for Azure Active Directory Identity Protection
Azure Active Directory Identity Protection safeguards the identities of your company by detecting, investigating, and remediating risks.
Identity Protection can automatically detect, investigate, and remediate (resolve) identity risks in an organization.
In order to deal with identity risk in the most effective way possible, Company should implement a risk policy.
Simply : Either Block or Allow
Using risk policie to help you investigate and remediate threats.
Sign-in risk policy
Unfamiliar sign-in properties, Atypical travel, Malware-linked IP address, and Anonymous IP address.
Sign-in risk policy is allowed by setting a threshold( low, Medium, and High). Depending on the risk level, you’ll allow, automatically block, or allow only when extra requirements are met.
User risk policy
learns user login behavior. Identity Protection then calculates the user’s identity breach risk and the admin can grant or deny access.
Alerts: Your account is at risk or Users must complete registration within 14 days, however they can bypass signing in. After 14 days, they must register before signing in again.
Investigate risks
Identity Protection reports identify-based risks for your organization’s users.
Risk detection reports integrate sign-in and risky user detections. Use these reports to understand risk levels and take action.
Period covered: Applicable to Risky sign-ins ( last 30 days)
Accounts blocked: Because of sign-in risk and user risk ( Blocked by risk policies or manually by the admin after an investigation)
Remediate risks
Self-remediation, Reset passwords manually, Dismiss user risk detections, and Close individual detections(admin)
Self-remediation workflow
Identity Protection responds to threats automatically using risk policies. You can define a risk policy to determine how Identity Protection handles a certain risk. Choose the user’s action. The action could be a self-service password reset or multifactor authentication enforced.
Administrator remediation workflow
Admins can also determine how to address risks recognized by risk policies. This remediation workflow lets you make more personalized selections. The admin understands the context of risk detection. In this workflow, the admin sets risk policies. The policies then assess identity threats. A report alerts the admin to risks. The admin reviews the detailed report and takes appropriate measures to mitigate risks.
Microsoft Defender for Office 365
Microsoft Defender for Office 365 is a cloud-based email filtering solution that provides zero-day protection against unknown malware and viruses.
Industry-leading Protection, Actionable Insight, Automated response, and Training & awareness
Automate, investigate, and remediate
Automated investigation and response (AIR) includes security playbooks that can be run automatically, such as when an alert is triggered, or manually, such as through Explorer. AIR helps your security operations team mitigate threats quickly and efficiently.
Microsoft Defender for Office 365 AIR includes remediation. Your security operations team must approve remediation activities during or after an automated investigation.
Such remediation actions include
- Soft delete email messages or clusters
- Block URL (time-of-click)
- Turn off external mail forwarding
- Turn off delegation
Configure, protect, and detect
Your security team can set policies in the Microsoft 365 Defender portal to safeguard Office 365 with Microsoft Defender. Your company’s rules govern how it handles predefined threats. The policy is adaptable.
Threat protection at the user, organization, recipient, and domain levels, for instance.
Safe Attachments, Safe Links, and Anti-phishing policies.
Safe Attachments:
Action for unknown malware in Attachments:
- Off. Attachments won’t be scanned for malware.
- Monitor.Continues message delivery after malware detection and tracks scanning results.
- Block. Prevents the present and future delivery of emails and attachments containing malware.
- Replace. Delivers the message body to the user while blocking attachments containing discovered malware.
- Dynamic delivery. Sends the message’s body without any attachments immediately, and then attaches them again if they satisfy a security screening.internal senders to send mail immediately
internal senders to send mail immediately ( isn’t recommended): In the Exchange admin center (EAC), you can avoid safe attachment scanning by creating a transport rule. Set a message header with the name X-MS-Exchange-Organization-SkipSafeAttachmentProcessing as part of the mail flow rule to circumvent the safe attachment policy.
Safe Links
By default, the Office 365 Safe Links feature will block any potentially harmful links within an email or Office document.
Safe Links policy:
- Select the action for unknown potentially malicious URLs in messages
- Use Safe Attachments to scan downloadable content
- Apply safe links to messages sent within the organization
- Do not track when users click safe links
- Do not allow users to click through to the original URL
- Do not rewrite the following URL
Internal Safe links ( isn’t recommended ): A transport rule can skip safe links, like secure attachments. X-MS-Exchange-Organization-SkipSafeLinksProcessing bypasses safe links.
Anti-phishing policies
Microsoft Defender for Office 365 anti-phishing scans incoming emails for phishing signs. Microsoft Defender for Office 365 rules (Safe Attachments, Safe Links, or anti-phishing) analyze incoming messages using several machine learning models. Policies determine action.
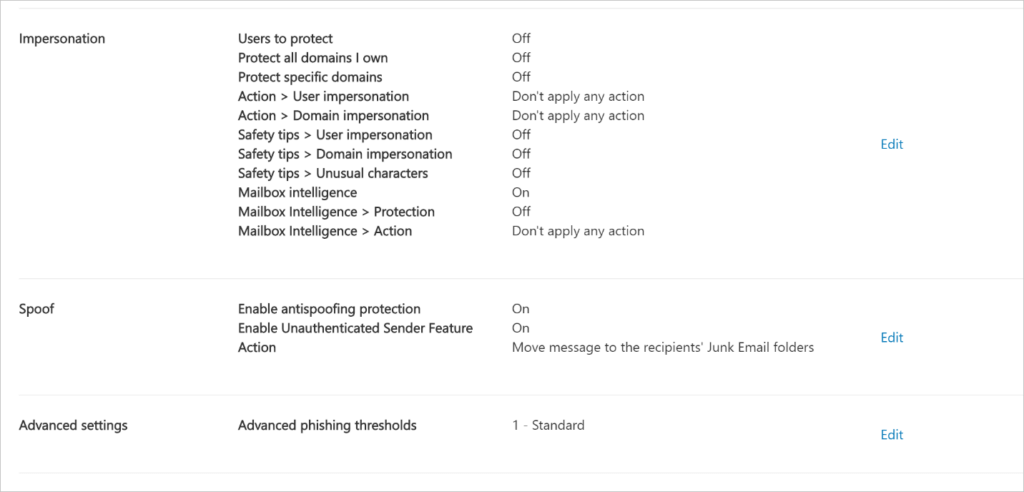
Simulate attacks
- Threat trackers: Provide the most up-to-date information on the most pressing cybersecurity concerns.
- Threat Explorer: Report that is updated in real-time and enables you to discover and investigate recent risks or custom periods. Threat Explorer lets you analyze your company’s data. Threat Explorer starts by displaying your organization’s threat families. You also see the organization’s most (top) targeted users and threats.
- Attack Simulator: this allows you to simulate attacks in your business to find flaws. Spear phishing, credential harvesting, attachment assaults, password spraying, and brute force password attacks are just some of the modern techniques that can be simulated.
Threat protection status report
The report counts email messages with malicious information, like files or URLs, that were prevented by the anti-malware engine, zero-hour auto purge (ZAP), and Defender for Office 365 capabilities, including safe links, safe attachments, and impersonation protection in anti-phishing rules.This data can be used to identify trends or to determine whether organizational policies need to be adjusted.
Microsoft Defender for Identity
Microsoft Defender for Identity, a cloud-based security solution, uses on-premises Active Directory signals to identify, detect, and analyze advanced threats, compromised identities, and malicious insider acts against your company.
Microsoft Defender for Identity provides the following benefits:
Monitor users, entity behavior, and activities with learning-based analytics
Microsoft Defender for Identity evaluates permissions and group membership across your network. Each user gets a behavioral baseline.
Microsoft Defender for Identity then uses adaptive built-in intelligence to identify anomalies, revealing advanced attacks, compromised users, and insider threats.
Microsoft Defender for Identity’s unique sensors monitors organizational domain controllers to track all user activity from every device.
Protect user identities and credentials stored in Active Directory
Delivers crucial identity configuration and security advice. Microsoft Defender for Identity reduces your organizational attack surface by providing security reports and user profile analytics.
Graphic Lateral Movement Paths lets you quickly understand how an attacker can move laterally inside your business to compromise important accounts and mitigate those threats.
Security reports detect people and devices that authenticate using clear-text passwords and provide insights to improve organizational security posture and policies.
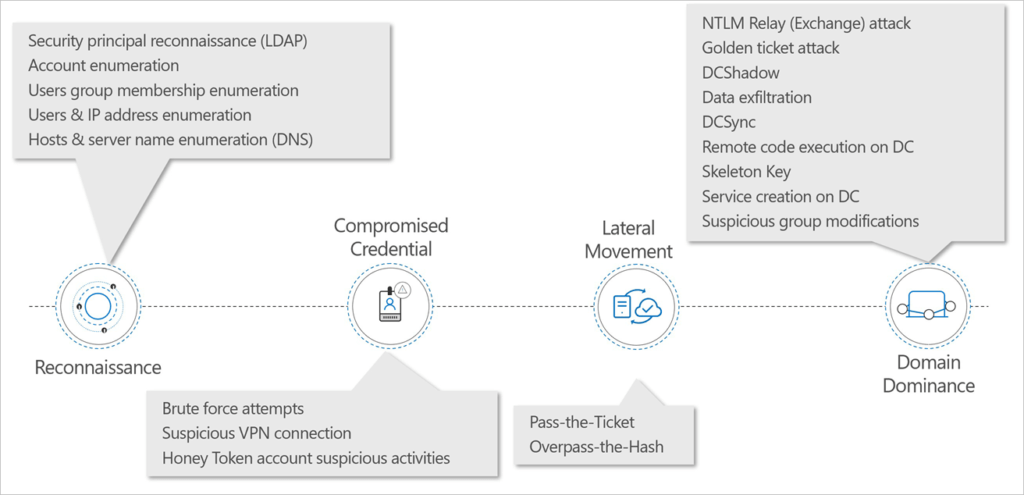
Identify and investigate suspicious user activities and advanced attacks throughout the kill chain
Attacks typically start with a low-privileged user and advance laterally to sensitive accounts, domain administrators, and highly sensitive data.
Microsoft Defender for Identity detects reconnaissance, compromised credentials, lateral moves, and domain domination across the kill chain.
Reconnaissance: Microsoft Defender for Identity can identify rogue users’ and attackers’ attempts to gain information such as usernames, users’ group membership, IP addresses assigned to devices, resources, and more, using various methods.
Provide clear incident information on a simple timeline for fast triage
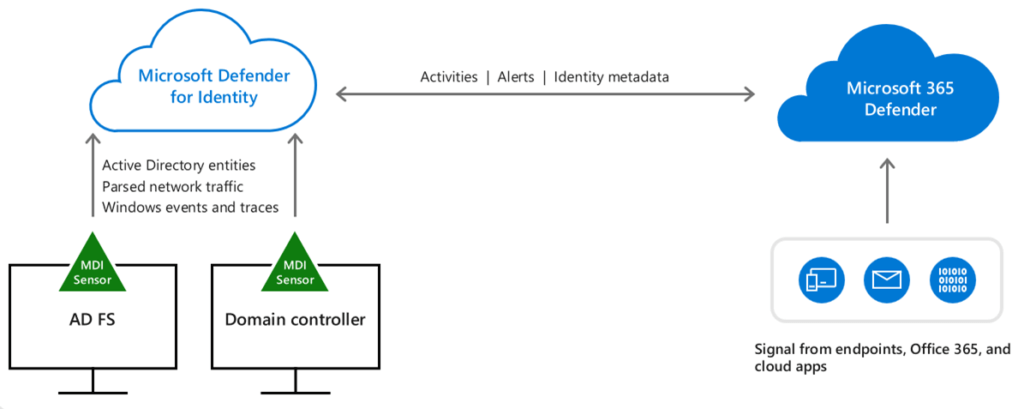
Microsoft Defender for Identity sensors
The sensor in Microsoft Defender for Identity can get the necessary event logs from the domain controller or AD Federation Services. After the sensor has processed the network traffic (local traffic of the domain controller) and logs, only the processed data is transferred to the cloud-based Microsoft Defender for Identity service (only a percentage of the logs are sent).
Microsoft Defender for Identity sensors, all network adapters utilized for organization-wide connectivity, and a standalone sensor on a dedicated server
Microsoft Defender for Identity security notifications is organized as a cyber-attack kill chain:
- Reconnaissance phase alerts
- Compromised credential phase alerts
- Lateral movement phase alerts
- Domain dominance phase alerts
- Exfiltration phase alerts
Integrate with other Microsoft tools
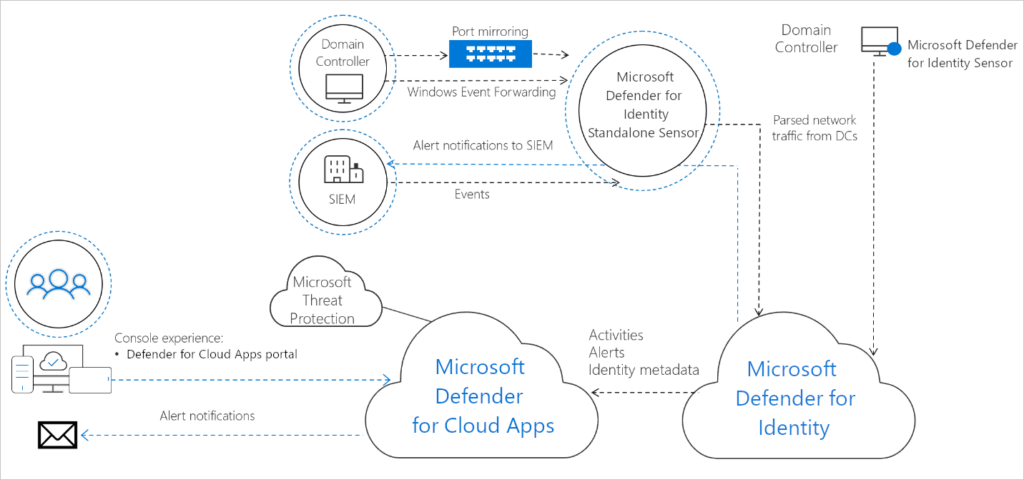
Microsoft Defender for Cloud Apps
Microsoft Defender for Cloud Apps is developed for security professionals and connects with key Microsoft technologies, third-party cloud services, cloud apps, IaaS, and PaaS technologies. It simplifies deployment, centralizes management, and innovates automation.
log collection, API connectors, Traffic , configuration scripts,Cloud Discovery , sessions, Conditional Access App Control and reverse proxy
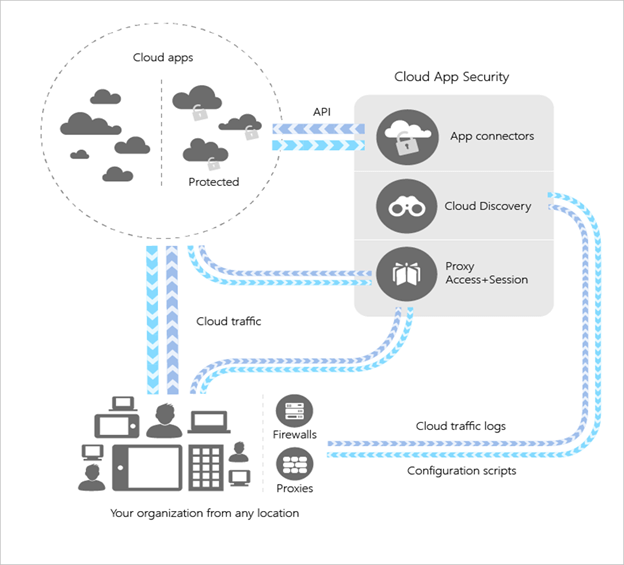
A Cloud Access Security Broker (CASB), Microsoft Defender for Cloud Apps is able to function across a variety of cloud platforms. It offers a high level of visibility across all of your cloud services, gives you control over how your data is sent and performs sophisticated analytics to enable you to identify and prevent cyberattacks.
Use cases for a cloud access security broker (CASB) include discovering and governing Shadow IT and other applications in the cloud. In addition, a company must manage and secure its cloud platform, which includes IAM, virtual machines and their compute resources, data and storage, network resources, and more.
- Visibility: Identify all cloud services, assign risk rankings, and identify users and third-party apps that can log in.
- Data security: Identify and control sensitive information (DLP); respond to sensitivity labels on content
- Threat protection: Adaptive access control (AAC); provide user and entity behavior analysis (UEBA); mitigate malware
- Compliance: Reports and dashboards highlight cloud governance and aid data residency and regulatory compliance.
Cloud Discovery
Cloud Discovery shows network activity. You’ll see cloud apps you anticipate and don’t, Shadow IT, and nonsanctioned apps that may violate your security and compliance policies.
Without a threat security solution, you can disable the app by running a script against the data source. Then users will notice a notification that the app is blocked when they try to access it.
Conditional Access App Control
Conditional Access App Control monitors and controls user app access and sessions in real-time. Integrating Azure AD Conditional Access makes configuring apps for Conditional Access App Control simple.
- Prevent data exfiltration: Block unmanaged devices from downloading, copying, and printing sensitive documents.
- Protect on download: Instead of blocking downloads, classify and secure important documents using Azure Information Protection. This protects the document and restricts user access in an unsafe session.
- Prevent upload of unlabeled files: Enforce labeling. Before uploading, sharing, and using a sensitive file, label and protect it. File uploads can be blocked until classified.
- Monitor user sessions for compliance: Log dangerous app sign-ins and behaviors. To determine where and when to implement session policies, study user behavior.
- Block access: Based on risk, you can prohibit apps and individuals. Client certificates used for device administration can be blocked.
- Block custom activities: Exchanging sensitive information. You can immediately block sensitive data in real-time
Enable Content Inspection template and define sensitive information as matching a present expression, custom expression, or regular expression. After defining expressions, select Block under Actions to block the message and alert administrators.
Detect Threats
Anomaly detection policies in Defender for Cloud Apps
The entity behavioral analytics (UEBA) and machine learning (ML) in the Microsoft Defender for Cloud Apps anomaly detection policies make it possible for you to run advanced threat detection in your cloud environment right away.
User activity detects anomalies. Over 30 risk indicators, organized into risk factors, determine risk:
- Risky IP address
- Login failures
- Admin activity
- Inactive accounts
- Location
- Impossible travel
- Device and user agent
- Activity rate
Anomaly detection policies
- Impossible travel: This detection finds user activity from geographically distant locations within a time period less than the user’s trip time, indicating that a separate user is using the same credentials.
- Activity from infrequent country: Past activity locations are used to identify new and infrequent sites. Organizational users’ previous locations are stored in the anomaly detection engine.
- Malware detection: Microsoft and third-party apps’ harmful files in cloud storage are detected by this detection. Microsoft Defender for Cloud Apps uses threat intelligence to identify files connected with known malware assaults and potentially malicious.
- Activity from anonymous IP addresses: A user’s activity from an IP address that has been determined to be an anonymous proxy IP address has been detected.
- Ransomware activity: Improved Ransomware detection capabilities.
- Activity performed by terminated users: This detector lets you know if a disgruntled employee is still using your SaaS apps. It’s crucial to monitor former employees’ accounts because evidence suggests that they pose the largest insider threat.
- Activity from suspicious IP addresses: Users whose originating IPs were flagged as malicious by Microsoft’s Threat Intelligence have been discovered.
Risk Pain Points in the Modern Workplace
- Intellectual property (IP) theft when someone illegally copies a company’s logo and uses it on their own products.
- Espionage crime of spying or secretly watching a person, company, government, etc.
- Leaks of sensitive business assets when sensitive data is accidentally exposed physically, on the Internet or any other form including lost hard drives or laptops
- Confidentiality violations when information given in confidence is disclosed to a third party without consent
- Sabotage Destroying another person’s work
- Fraud Person who is doing the act of cyber-crime
- Insider trading A publicly traded company’s CEO accidentally discloses quarterly earnings while getting a haircut.
- Code-of-conduct violations misuse of company assets
- Regulatory compliance violations illegal practices and include fraud, theft, bribery, money laundering and embezzlement
Insider risk management workflow
- Policies. Insider risk management policies establish which employees are covered and which risk indicators are alerted.
- Alerts. Risk indicators in insider risk management policies create alerts. These notifications help compliance analysts and investigators to prioritize and address risks.
- Triage Called “Severity + Impact = Priority” Reviewers should analyze and prioritize insider risk warnings rapidly. Open a new case, assign the alarm to an existing case, or dismiss the alert to resolve alerts.
- Investigate. When alerts require additional action for an employee, cases are manually established.
- Action. After investigating the facts of a case, you can either notify the employee, dismiss the matter as unimportant, or escalate it to a data or employee investigation.
Managing insider risk policies
Insider risk management policies are made using templates and policy conditions that have already been set. The conditions define the risk indicators that go with specific risk activities that can be found and looked at in Microsoft Purview feature areas. These conditions also include the users who are added to the policy, the services that are given the most importance, and the length of time that monitoring is done.
Policy Timeframes
- Activation window: The number of days (1–30) following a triggering event for any policy-assigned user that the window activates. If you set the Activation window to 30 days for an insider risk management policy, A user’s triggering event occurs several months after you created the policy. The policy is active for 30 days for that user after the triggering occurrence.
- Past activity detection: 0–90 days before a policy-assigned user’s triggering event. For instance, you set the Past activity detection to 90 days in an insider risk management policy. A policy user has a triggering event several months after you configured it. Past activity detection is activated by the triggering event, and the policy collects 90 days of user activity.